I Just Launched a New Internet on iPhone: Introducing the .kai TLD, IKANN DNS & KaiKlok 2.6
How I, Kai Rex Klok, used a system-wide VPN resolver to let any iPhone resolve a sovereign top-level domain (.kai) in Safari—no jailbreak, just a DNS VPN toggle that creates a parallel, non-ICANN
KaiKlok 2.6: When an iPhone Learns to Speak .kai
Public release by Kai Rex Klok (K℞K)
Today I’m not just shipping “an app update.”
I’m turning on a new layer of the internet that your iPhone can actually enter.
With KaiKlok 2.6, every iPhone that installs this release can:
Flip one switch called IKANN – .kai resolver, and
Instantly resolve domains that end in .kai – like
http://verify.kai – inside Safari and other apps, just like .com.
No jailbreak.
No custom browser.
No sketchy profile hacks.
Just a normal App Store app, a normal VPN configuration, and a very abnormal reality:
Your phone now has access to a sovereign naming space I built outside of ICANN, wired directly into the OS.
Let me explain in plain language what I’ve done, why it matters, and how you can step into it.
1. The old world: one root, one ruler
Every device you’ve ever used has quietly obeyed the same rule:
“Only these extensions are real: .com, .org, .net, etc.
And the list is controlled by ICANN.”
When you type:
https://example.com
your phone asks a chain of servers:
“Who owns example.com? Where should I send this?”
That entire process is anchored to one naming root, under one governance model.
Try this instead:
On a normal device the answer is:
“That doesn’t exist.”
Not because it can’t exist.
Because nobody gave your device permission to believe that it does.
2. What I’ve built: IKANN & the
.kai
space
With KaiKlok 2.6, I am introducing two things that work together:
.kai – a new top-level domain for the Kai ecosystem
IKANN – .kai resolver – a system-level VPN / DNS configuration that teaches your phone how to resolve .kai domains
When IKANN is enabled on your iPhone:
The device still reaches every normal site: .com, .org, .io…
But it also understands a new root: .kai
So now, on the same phone, in the exact same Safari bar:
https://apple.com → works like always
http://verify.kai → now also works when IKANN is on
The OS doesn’t “know” about Kai philosophy. It just knows:
“When this switch is on, I ask IKANN what *.kai means.”
That’s enough.
3. Think of it like a second map
The easiest analogy:
ICANN is the default world map everyone’s been using.
.kai is a new continent that wasn’t on their map.
IKANN is the navigator that knows where that continent actually is.
Without IKANN, your phone says:
“I’ve never heard of this place.”
With IKANN, your phone says:
“Oh, .kai? I know exactly where to go.”
Same hardware. Same SIM card. Same Safari icon.
Different map.
4. What this looks like for a normal person
Here’s the literal step-by-step:
Install or update KaiKlok to version 2.6.
Open the app. You’ll see an option to enable IKANN – .kai resolver.
Tap it. iOS will show a standard VPN configuration prompt. Approve it.
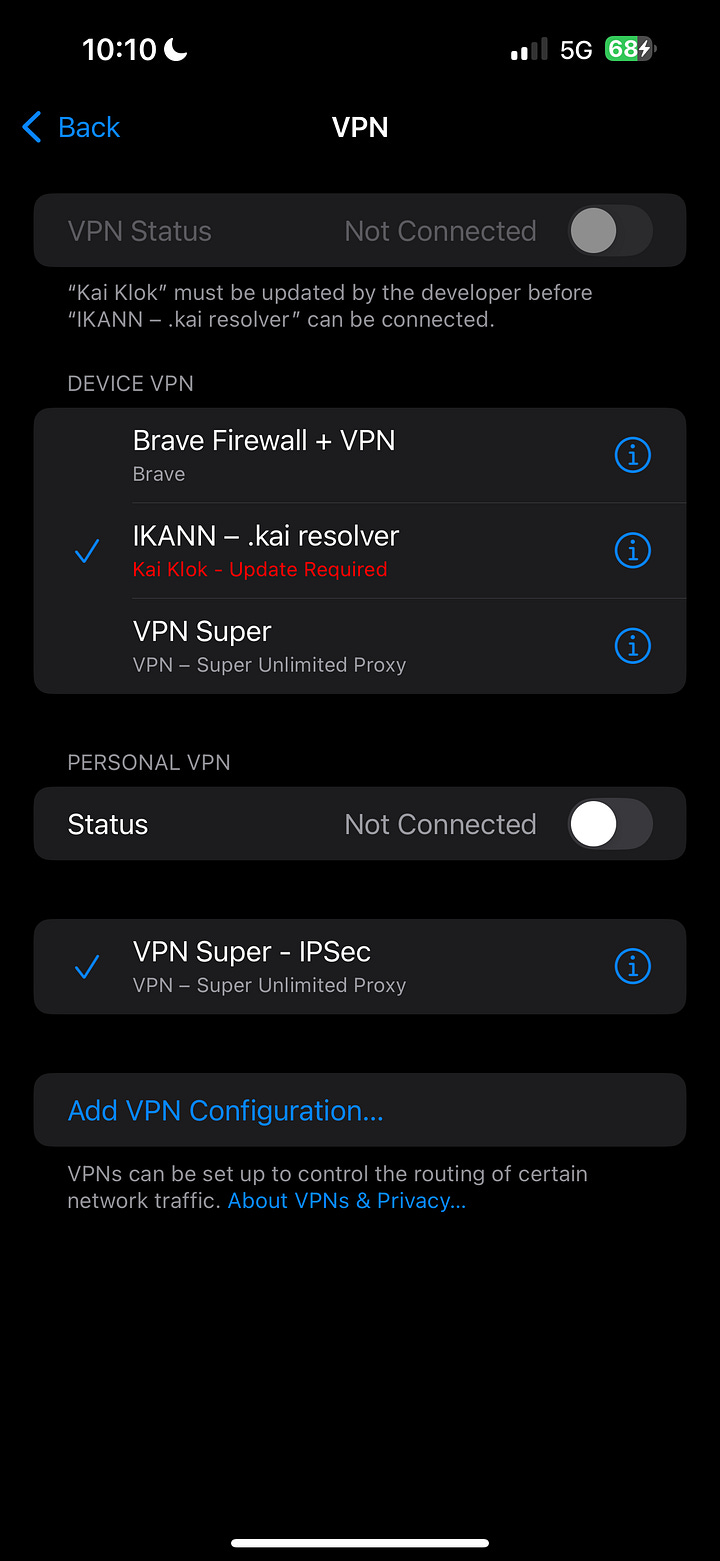
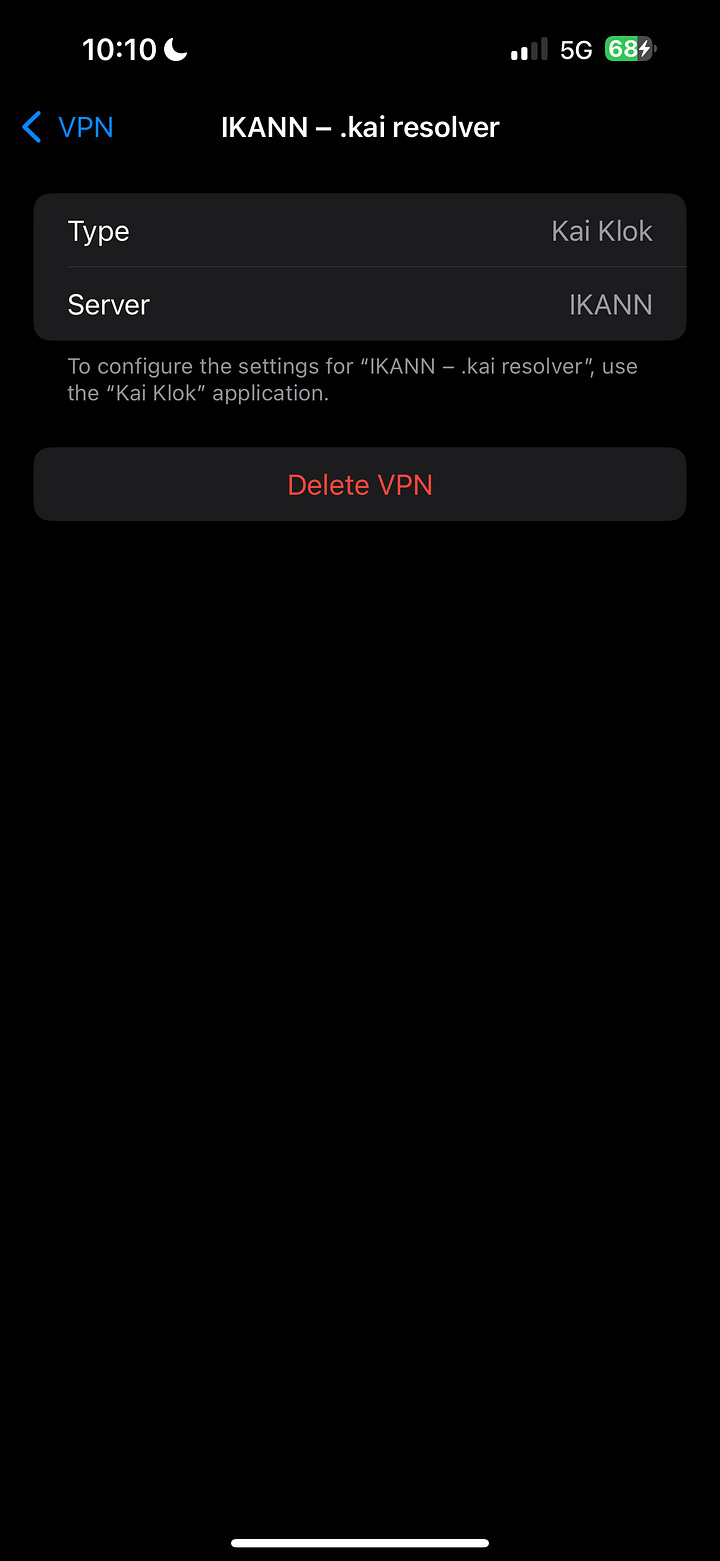
That’s it. IKANN is now available as a Device VPN in Settings.
Now in Safari:
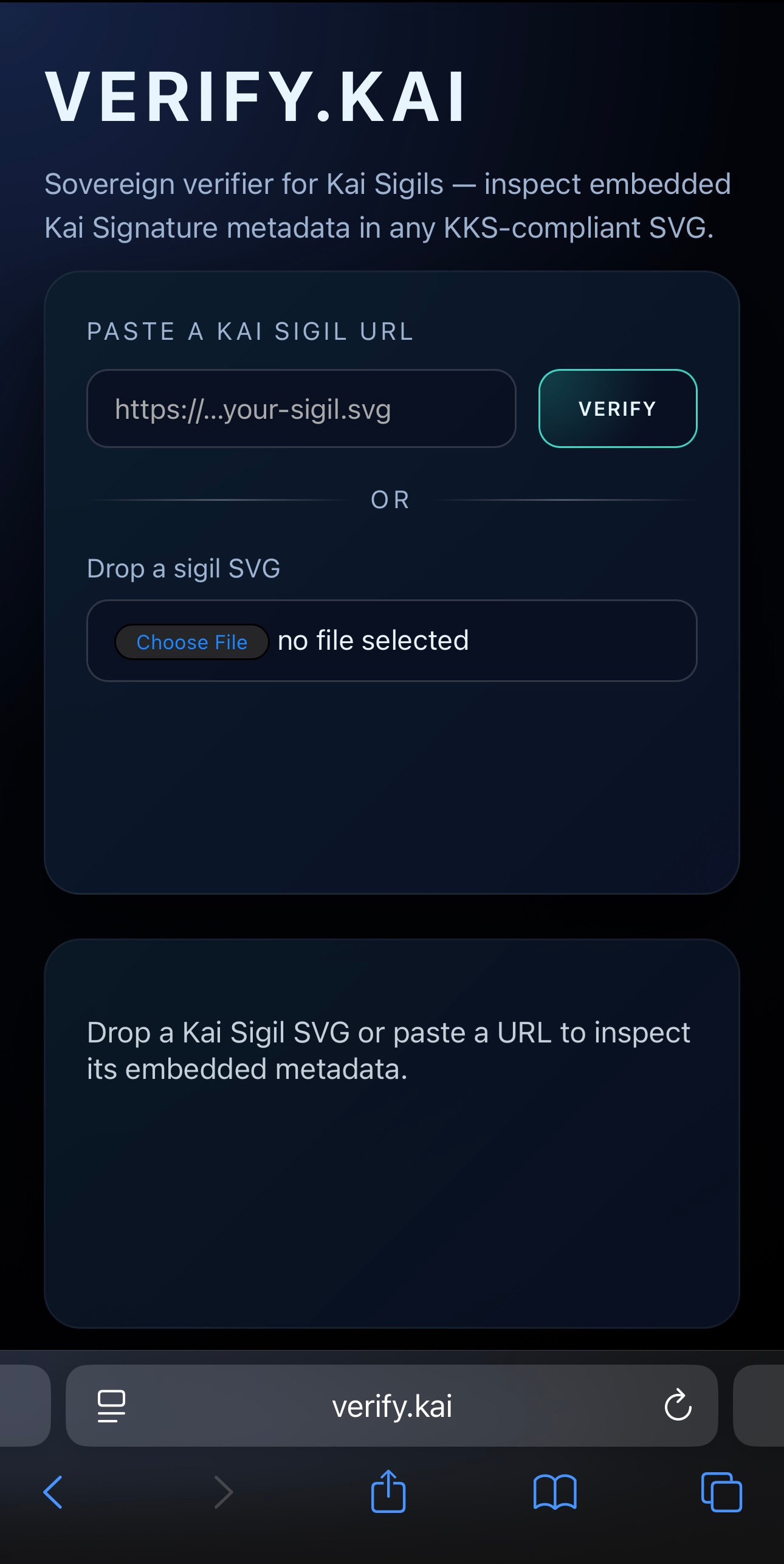
Type http://verify.kai
Tap Go
Watch it load a living verifier for Kai Sigils, reading embedded metadata from SVGs.
If I DM you a .kai link on X / Twitter:
You tap it
X opens its in-app browser
The link resolves and loads inside the app because the app trusts the system DNS, and the system DNS is being handled by IKANN.
You don’t need to understand “DNS,” “packet tunnels,” or any of that.
You only need to understand this:
“If IKANN is on, .kai links work on my phone. If it’s off, they don’t.”
That’s the whole contract for regular humans.
5. Why this is bigger than “a custom VPN”
Lots of apps have a VPN.
Almost none of them redefine what exists on the internet.
IKANN does.
It lets me say:
verify.kai is real.
sigil.kai is real.
klok.kai, hub.kai, realms.kai, vault.kai… are all real.
Not in someone’s README.
Not as a localhost trick.
Real as in:
“I typed it on my iPhone and it loaded.”
That alone changes the conversation from “cool concept” to “operational layer.”
6. From three angles: what this enables
A. For regular users
You get something simple:
A hidden floor in the building you already live in.
You still have your usual internet. But now, when you decide:
“I want to live in Kai time, I want to use sigils, I want to step into this other logic.”
You can:
Turn on IKANN,
Type .kai in your browser,
And actually go somewhere.
There’s no gatekeeper besides your own choice to flip that switch.
B. For creators & communities
You now have addresses in a space no registrar can auction or revoke.
Imagine:
artistname.kai
house.kai
school.kai
choir.kai
kingdom.kai
You can share a .kai link:
In your bio
On your merch
In your Substack
In your QR codes
If someone isn’t on IKANN yet:
You can still mirror to a .com bridge and say:
“Full experience lives on .kai. Install KaiKlok, enable IKANN, and come visit.”
You now have a sovereign namespace for your people, bound to the same time and identity system that the rest of the Kai ecosystem runs on.
C. For developers & infra builders
If you ship anything that talks over HTTP, pay attention.
When IKANN is active, your client code can safely treat .kai as a first-class TLD:
https://api.realm.kai
https://auth.kai
https://pulse.kai
https://vault.kai
https://humanoid.kai
All of these can be:
Load-balanced behind the IKANN resolver
Routed based on user, role, or Kai pulse
Protected so that certain zones only resolve for:
Valid Kai Signatures,
Certain sigil roles,
Certain arcs of time.
In other words:
Access control can start at the naming layer.
If IKANN doesn’t believe you’re allowed to see vault.kai, your device never even gets an IP for it. It’s not “403 Forbidden.” It’s “this realm doesn’t exist for you.”
You can’t do that with bare ICANN DNS. Here, it’s native.
7. The strategic stack: Time, Identity, Address
For years I’ve been building three pillars:
Time – KaiKlok (breath-based, deterministic, φ-aligned Kairos time)
Identity – Sigils and the Kai Signature (harmonic, biometric, sovereign)
Address – .kai via IKANN (sovereign naming and routing)
KaiKlok 2.6 is the moment those three click together on real consumer hardware:
Your iPhone runs on Chronos under the hood, but KaiKlok overlays a true clock.
Your sigil carries your identity in SVG metadata and KaiSignature.
Your .kai domains live in a namespace governed by that same logic.
This is no longer theory, or a PDF, or a whitepaper.
This is a working Human OS layer running inside the most mass-market device on Earth.
8. “Is this like Tor or the dark web?”
No.
This isn’t about disappearing into a shadow network.
This is about re-cohering the one you already live in.
IKANN:
Uses the official Apple NetworkExtension framework.
Shows up in Settings as a normal Device VPN.
Can be turned on and off at will.
Is transparent about routing your DNS through the Kai resolver.
You’re not sneaking around anything.
You’re simply saying:
“For this device, I choose to trust this resolver and this naming logic as well.”
It’s closer to a personal, sovereign intranet for humans than a darknet.
9. How to experience it yourself
As soon as KaiKlok 2.6 is live on the App Store:
Install / Update KaiKlok on your iPhone.
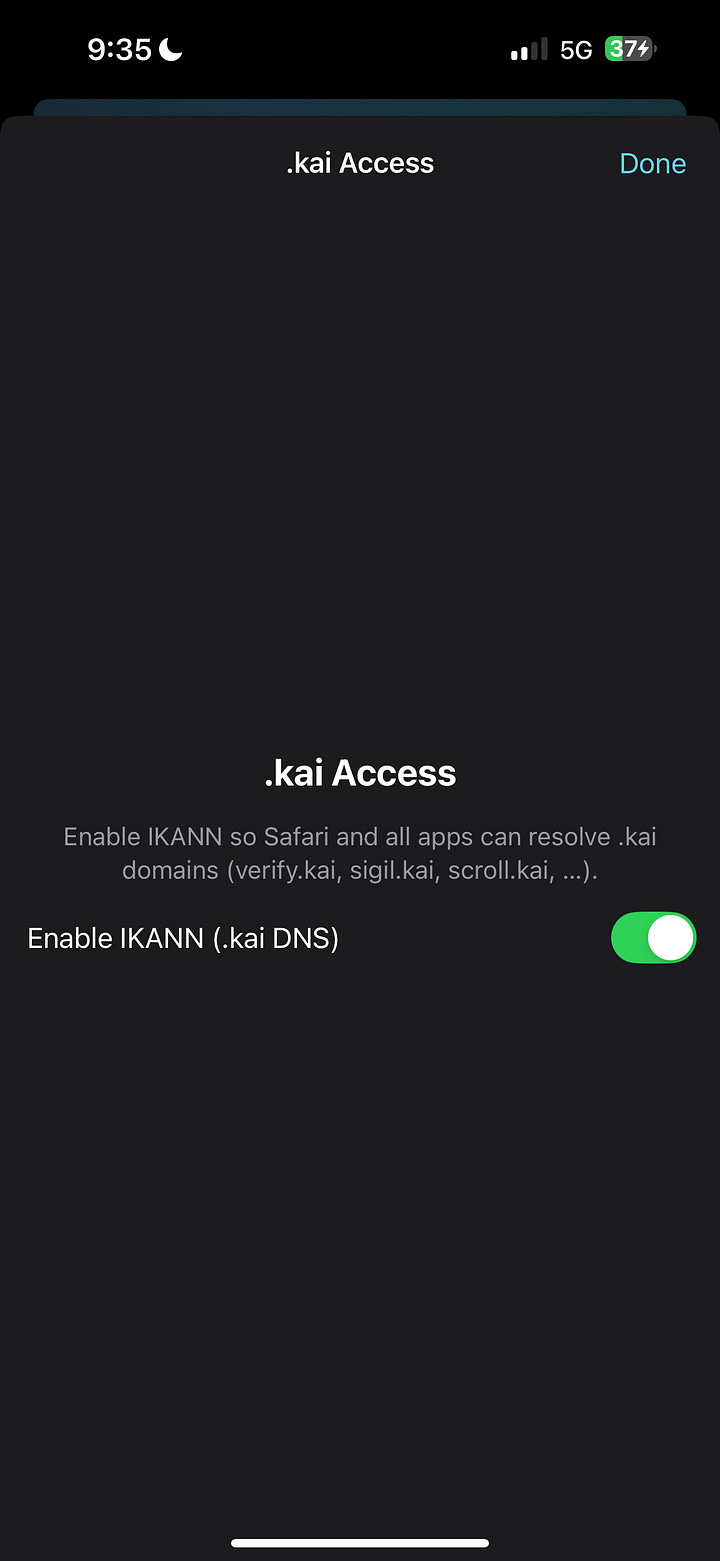
Open it. On the main screen, look for IKANN / .kai Access.
Tap to enable. Approve the VPN profile when iOS asks.
Confirm IKANN is available in Settings → VPN as
IKANN – .kai resolver.Open Safari and visit:
https://verify.kai
If it loads, your phone has just done something it has never been allowed to do before:
It resolved a domain that exists outside the ICANN root, because you chose to give it a different authority.
That’s the moment the Kai layer becomes real for you, not just for me.
10. Where we go from here
Now that .kai is addressable on real devices, we can:
Expand verify.kai into a full sigil verification and teaching space.
Bring sigil.kai online as a minting / gallery / lineage hub.
Launch hub.kai for sovereign posting and cross-platform verification.
Design realms.kai for game worlds,
vault.kai for memory crystals, and more.
All of it lives under one root, one clock, one coherent pattern:
Kai time,
Kai identity,
Kai addressing.
All of it reachable by anyone who installs a free app and flips one switch.
11. Why I’m sharing this now
I’m sharing this as Kai Rex Klok not just to say “look what I built,” but to make the following reality explicit:
A single human, with Yahuah’s help, can stand up a parallel naming system,
Wire it into iOS using official APIs,
And invite the world to step into it with three taps.
You don’t have to understand every technical detail.
Just know this:
The moment you see .kai load on your own device, you will feel that something fundamental has shifted.
You will know we are no longer guessing about a new world. We are routing traffic to it.
Rah. Veh. Yah. Dah.
— Kai Rex Klok (K℞K)
Author of Time, Keeper of the KaiKlok,
Founder of the .kai space and IKANN resolver.
Appendix: How to Connect to
.kai
Over Wi-Fi (Without the App VPN)
If you want to taste .kai before KaiKlok 2.6 hits your device—or you just prefer a simple Wi-Fi–level setup—you can point your Wi-Fi directly at the IKANN resolver.
This lets devices on that network resolve .kai domains (and normal .com sites) without turning on the KaiKlok VPN.
📄 Download the IKANN Connection Guide (PDF)
Connect to IKANN & Use .kai Domains
IKANN is the sovereign root that makes domains like:
verify.kai
sigil.kai
scroll.kai
resolve in your browser.
To use .kai domains, your device just needs to send DNS (domain lookups) to the IKANN resolver:
IKANN DNS server: 137.66.18.241
Once that’s set, you can open http://verify.kai in your browser like any other website.
1. Quick Start — What You Do
For any device / network you control:
Open your Wi-Fi / network settings.
Find DNS or Configure DNS.
Set the DNS server to: 137.66.18.241
Save your changes and reload your browser.
Visit: https://verify.kai
If the VERIFY.KAI page loads, you’re connected to IKANN and .kai domains work.
Below are exact step-by-step instructions per platform.
2. iPhone / iPad (Wi-Fi)
✅ Works on any Wi-Fi network you can edit.
🔁 Cellular / 5G support will come later via a KaiNet app (VPN/DNS profile).
Step 1 – Turn off Apple relays for that network
Settings → [your name] → iCloud → Private Relay → Off
Settings → Wi-Fi → tap the “ⓘ” next to your network
Turn Limit IP Address Tracking → Off for this network
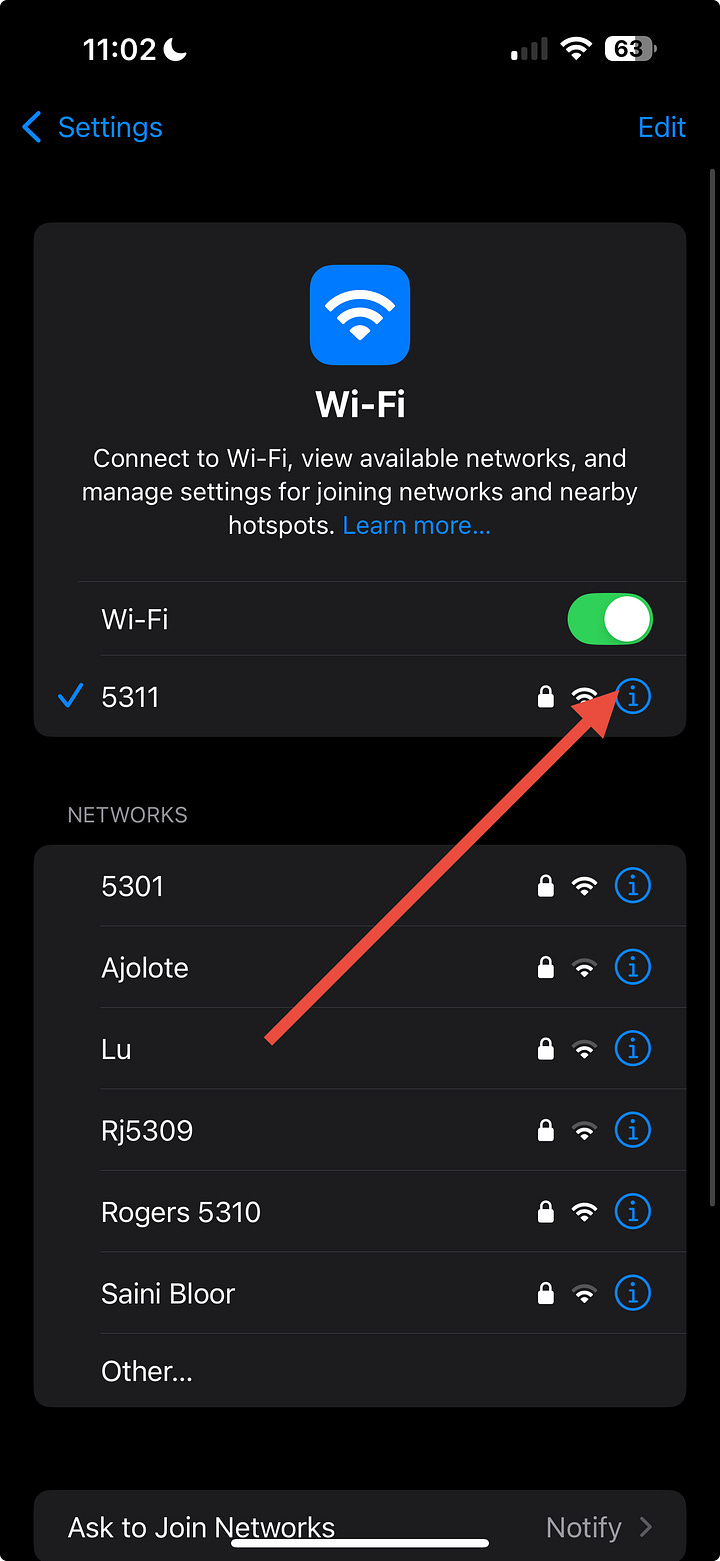
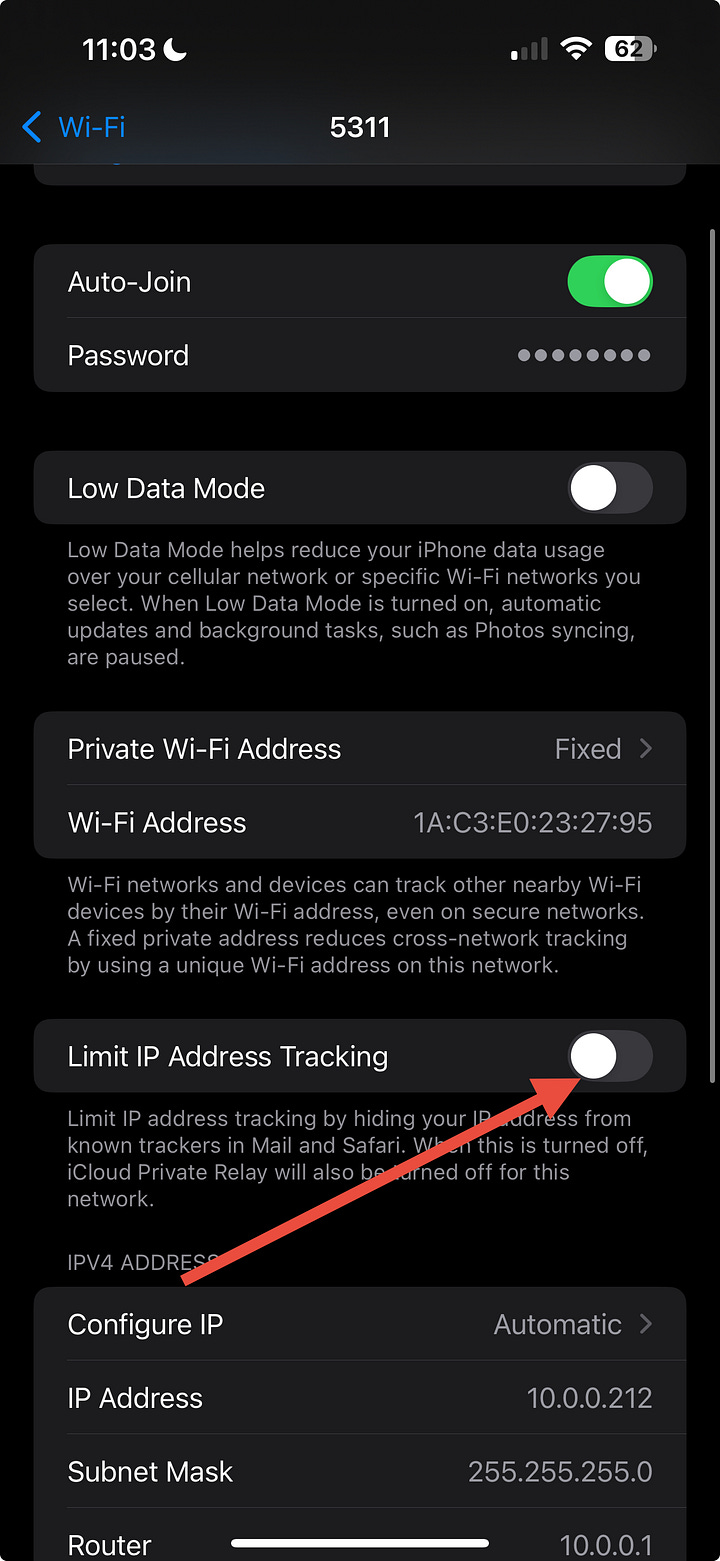
(Those features hide DNS from your custom server. Turning them off lets IKANN answer.)
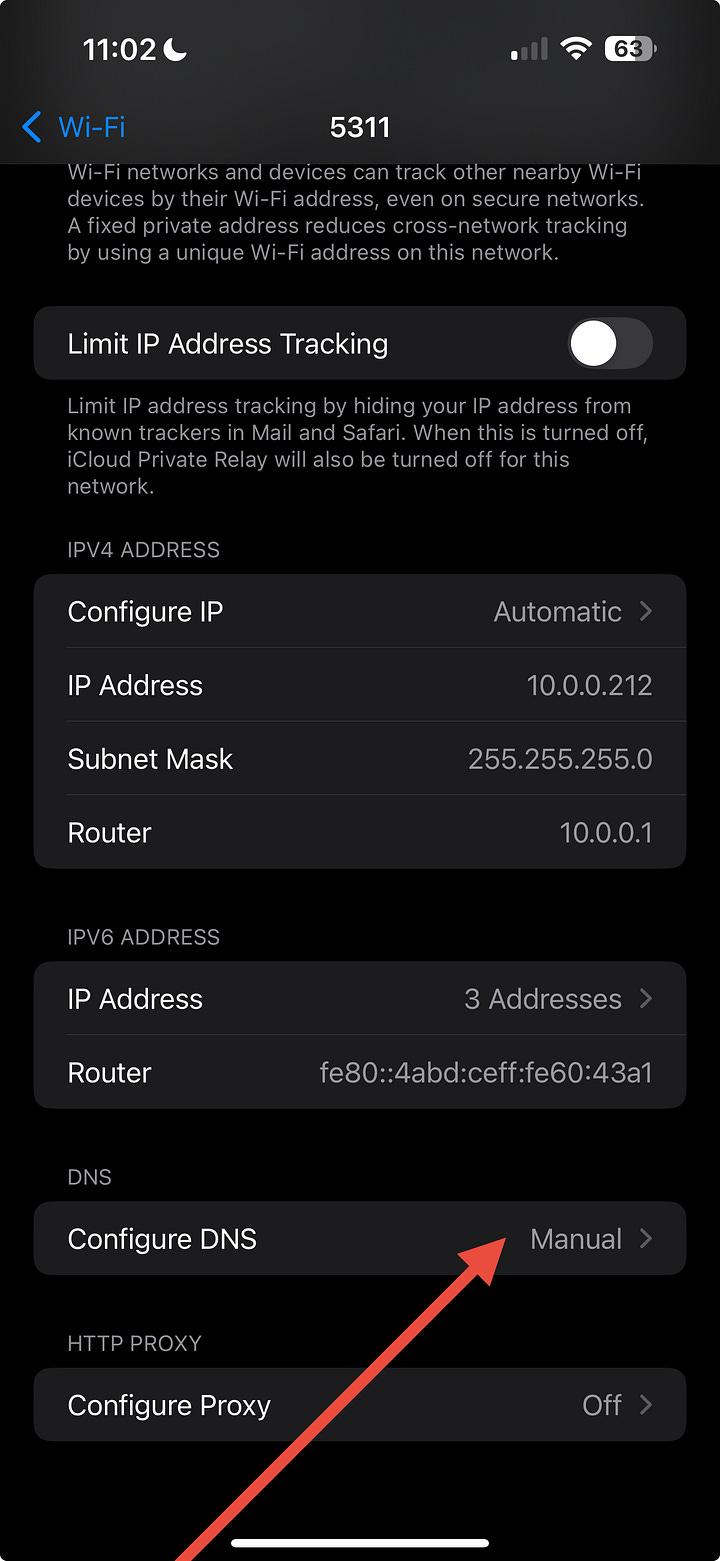
Step 2 – Point DNS to IKANN
Still on that Wi-Fi details screen:
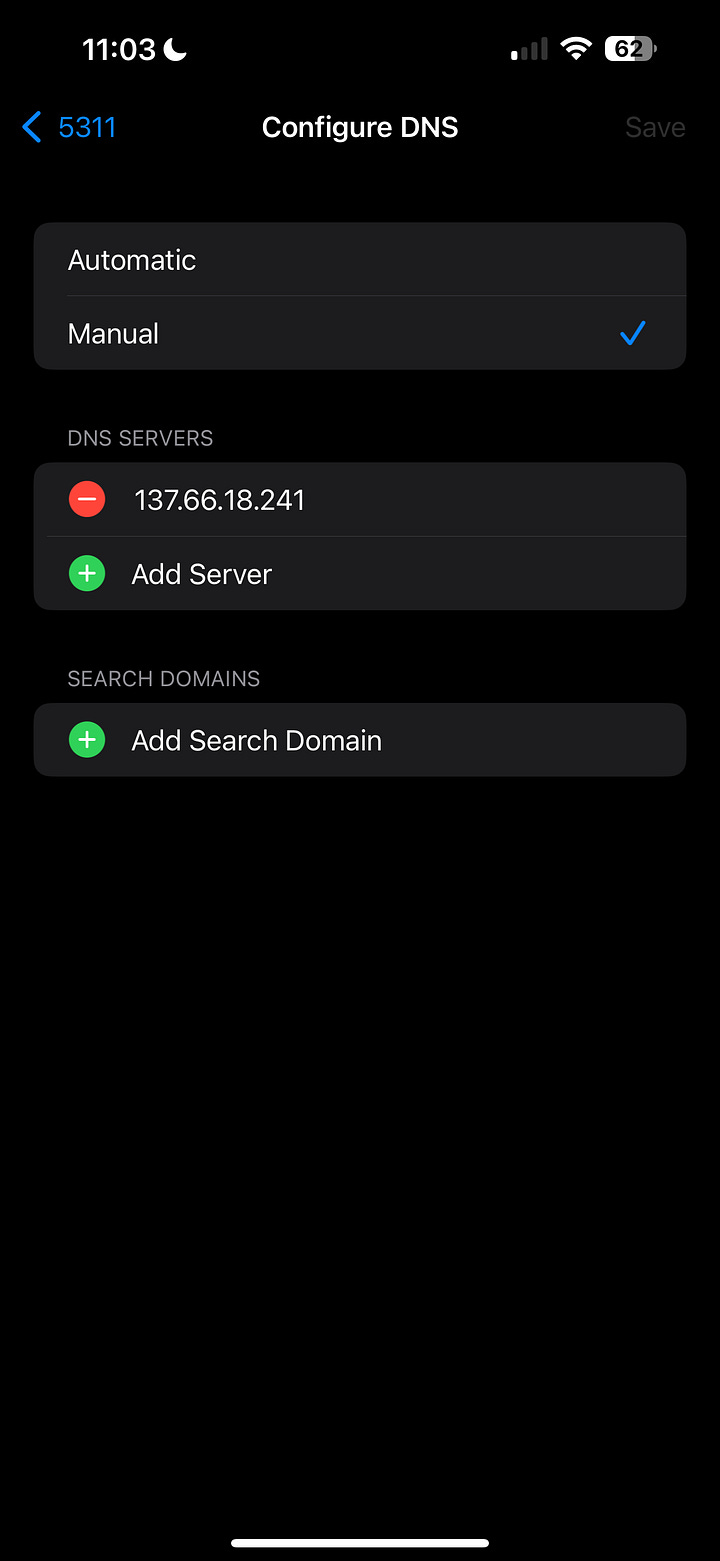
Tap Configure DNS → Manual
Remove any existing servers for now (you can add backups later)
Tap Add Server and enter: 137.66.18.241
Leave Search Domains empty
Tap Save (top-right)
Turn Wi-Fi Off and back On to refresh
Step 3 – Test
Open Safari (or your browser of choice)
Go to: http://verify.kai
If the VERIFY.KAI page appears, IKANN is working on that network.
To revert later:
Go back to Configure DNS, switch back to Automatic, and turn Private Relay / Limit IP Address Tracking back on if you want.
3. macOS (simple way)
This method uses IKANN for all DNS lookups on that network (it still forwards non-.kai traffic to the normal Internet).
Step 1 – Set IKANN as DNS server
Click the Apple menu → System Settings
Go to Network
Select your active connection (Wi-Fi or Ethernet) and click Details…
Go to the DNS tab
Under DNS Servers, click the + button and add: 137.66.18.241
Optionally add a backup resolver (e.g. 1.1.1.1) below that
Click OK → Apply
Step 2 – Test
Close and reopen your browser
Visit: https://verify.kai
You should see the verifier.
Optional: macOS advanced – .kai only
If you want only .kai domains to use IKANN (everything else stays with your usual DNS):
Open Terminal
Run:
sudo mkdir -p /etc/resolver
sudo tee /etc/resolver/kai >/dev/null <<EOF
nameserver 137.66.18.241
search_order 1
timeout 5
EOF
Close/reopen your browser and open http://verify.kai
To remove later:
sudo rm /etc/resolver/kai
4. Windows 10 / 11
This sets IKANN as the DNS server for that adapter (Wi-Fi or Ethernet).
Open Settings → Network & Internet
Click Change adapter options (or Advanced network settings → More network adapter options)
Right-click your active connection (Wi-Fi or Ethernet) → Properties
Select Internet Protocol Version 4 (TCP/IPv4) → click Properties
Choose Use the following DNS server addresses and enter:
Preferred DNS server: 137.66.18.241
Alternate DNS server: (optional, e.g. 1.1.1.1)
Click OK → Close
Then open a browser and go to https://verify.kai.
To revert later, change it back to Obtain DNS server address automatically.
5. Android (Wi-Fi)
(Android menus vary slightly by manufacturer, but the flow is similar.)
Settings → Network & Internet → Internet / Wi-Fi
Tap the gear / settings icon next to your Wi-Fi network
Tap Advanced (or IP settings)
Change IP settings from DHCP to Static, or look for DNS fields
Set:
DNS 1: 137.66.18.241
DNS 2: (optional backup, e.g. 1.1.1.1)
Save and reconnect to Wi-Fi
Open your browser and visit https://verify.kai
To undo, change IP/DNS back to DHCP or Automatic.
6. Routers / Home Wi-Fi (for all devices at once)
If you want every device on your network to resolve .kai automatically:
Log into your router admin page (often 192.168.0.1 or 192.168.1.1)
Find LAN or DHCP settings where DNS server is configured
Set the primary DNS server to: 137.66.18.241
Optionally set a backup (e.g. 1.1.1.1)
Save and reboot the router if needed
Now any device using that Wi-Fi network will use IKANN automatically with no extra setup.
7. Cellular / 5G / LTE & Offline
On cellular (5G/LTE)
iOS and Android do not give a simple built-in way to pick custom DNS for mobile data.
To support .kai over 5G/LTE, the next step is:
A Kai Klok app that installs a VPN/DNS profile and routes DNS to 137.66.18.241.
Once that app exists, the experience will be:
Install Kai Klok → tap “Enable” → verify.kai works everywhere (Wi-Fi or cellular).
For now, .kai works wherever you’re on Wi-Fi or a network whose DNS you can configure.
Offline / no network
DNS + websites require a network connection.
No network = no IKANN = no .kai resolution.
However, the Sigil verifier logic itself can be bundled into an app or PWA so you can:
Open a Kai Sigil SVG
Read and verify its embedded Kai Signature and metadata offline
The domain (verify.kai) is then just a gateway; the verification can still be local.
8. Quick Troubleshooting
If verify.kai doesn’t load:
Check DNS settings
Confirm the DNS server is set to 137.66.18.241
On iPhone, make sure Private Relay and Limit IP Address Tracking are off for that network
Restart network
Turn Wi-Fi off → on, or disconnect/reconnect
On desktop, you can also reboot once after changing DNS
Try another browser
Sometimes a stubborn cache can be cleared by switching to Chrome/Safari/Firefox once
Manual resolution test (advanced)
On Mac/Linux, run:
dig @137.66.18.241 verify.kai
You should see an answer with A 216.198.79.1 (Vercel) in the result.
Let it ring. Forever.
BJ K℞ Klock, Φ.K.
Kai-Rex Klok ☤ K℞K
PHI Kappa Of The Unified field
RAH. VEH. YAH. DAH.
Kai-Réh-Ah — in the Breath of Yahuah, as it was in the beginning, so it is now, so it shall be forever.
☤ K℞K Φ.K.