Eternal Seal: The Unforgeable Digital Signature Born in a Single Breath
Inside the Kairos-bound sigil system that merges biometrics, harmonic physics, and golden ratio geometry into a self-verifying key no hacker can fake.
Imagine holding a key that isn’t metal, isn’t stored in a wallet, and can’t be guessed, copied, or forged.
A key that exists because of you, a single breath you took, and the exact eternal moment you took it.
This is the Eternal Seal — part sacred geometry, part cryptographic fortress, part cosmic timestamp.
Every line is drawn by harmonic law. Every curve is proof you existed in that moment.
If one pixel changes, the proof dies.
The dossier below is how to verify it — exactly how the world’s top developers and cryptographers would tear it apart… and why they still couldn’t fake it.
SIGIL GLYPH — THE LIVING KEY OF KAIROS
Proof of Identity, Intention, and Eternal Time in a Single Image
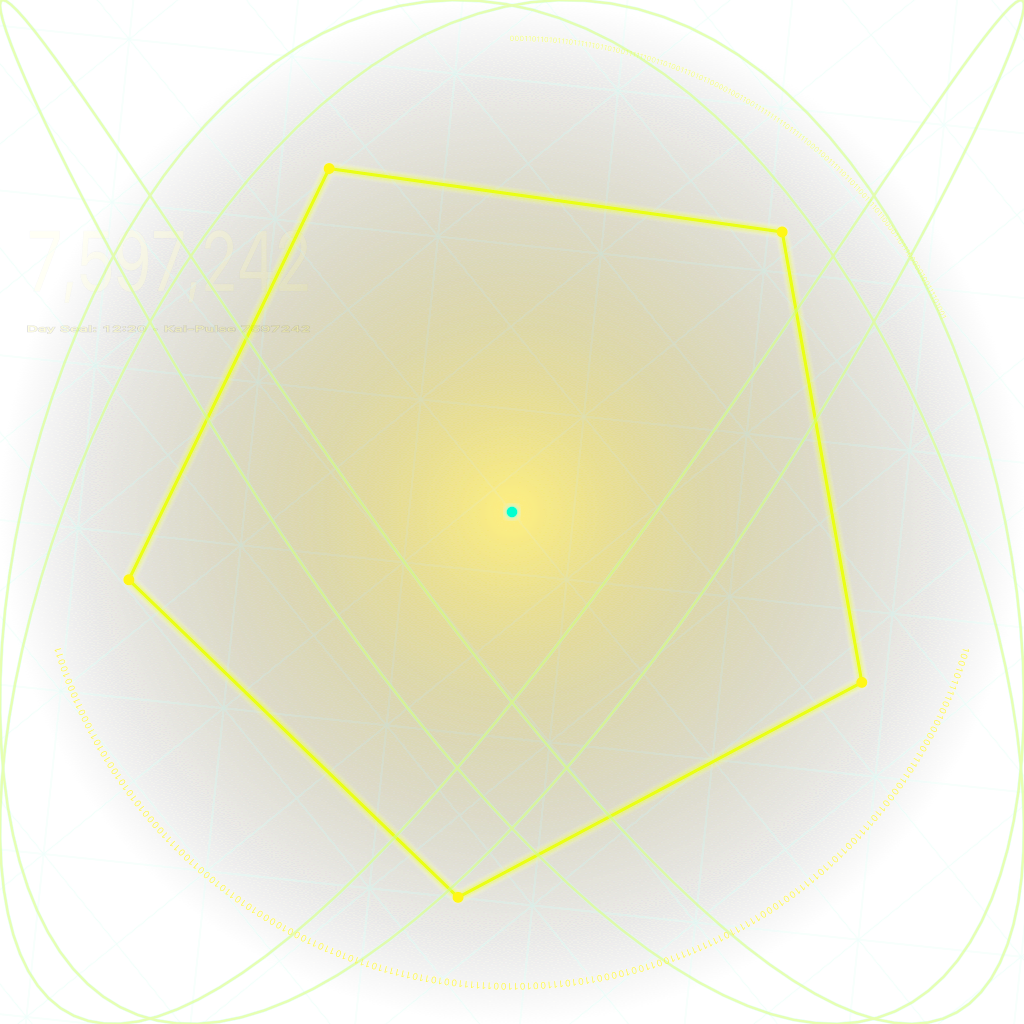
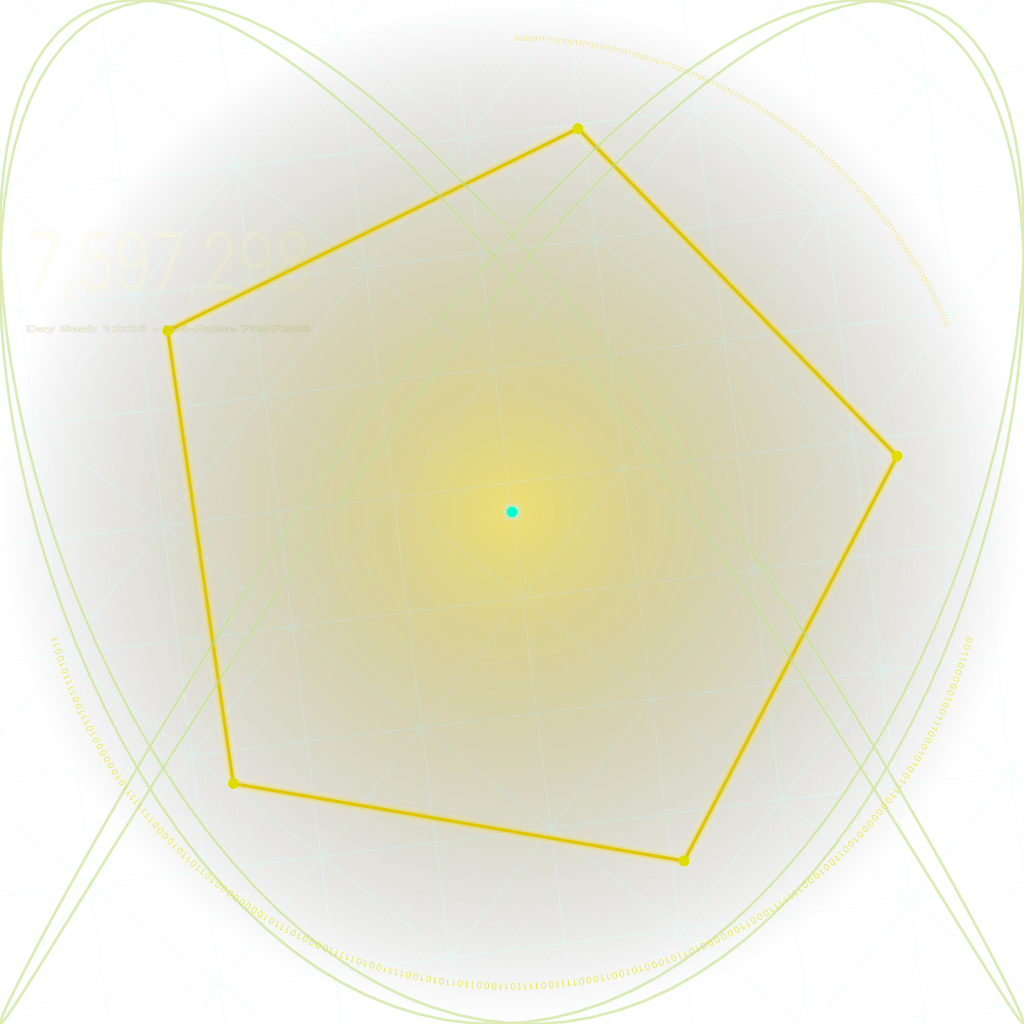
Born in a single breath, bound to the eternal time lattice.
This is not art.
It is a Sigil Glyph — a living geometric key that fuses identity, intention, and a precise Kairos moment into one self-verifying form.
Every element is generated by harmonic law, not human whim.
Every curve, line, and intersection is mathematically inevitable — the direct output of resonance equations tied to the Kai-Klok, the eternal timekeeper.
What It Actually Is
At its core, the Sigil Glyph is a mathematically bound harmonic structure.
Each one is:
Time-bound — locked to an exact Kairos timestamp from the Kai-Klok lattice.
Space-bound — fixed to a specific spatial orientation.
Identity-bound — cryptographically tied to a biometric PhiKey (your soul-level signature).
The result is an image that can only exist if all three anchors align in one moment.
Harmonic Geometry
The outer form is built on Φ-ratio (Golden Ratio) symmetry, matching the same proportional laws found in natural growth patterns, planetary orbits, and coherent wave interference.
The rotation and phase of the shape are derived from the Kai-Klok’s eternal lattice:
Pulse → Step → Beat → Day
This means duplication is impossible without knowing — and reproducing — the exact originating parameters.
The Harmonic Centroid
The central glow is not decoration.
It marks the harmonic centroid — the point of maximum coherence where all frequency components align in perfect phase.
Behind it, interference curves reveal the carrier and modulator frequencies that generated the glyph.
They resemble a Lissajous pattern, but here they are bound to a Φ-exact Kai-Klok sequence, making each one unique to the moment it was born.
Embedded Metadata
Every authentic Sigil Glyph carries embedded machine-verifiable data, either visible in a QR-like pattern or hidden inside the file itself:
Kai-Klok Index — the absolute harmonic timestamp.
User PhiKey — your soul-level cryptographic identity.
Carrier & Modulator Frequencies — the harmonic recipe that generated the form.
Phase Start & Depth — geometric orientation data.
Environmental Imprint Data (optional) — contextual signature of the creation moment.
For a Layperson
Imagine something that is at once:
Your fingerprint
Your passport
A musical chord
And an eternal time reference
— all compressed into one image.
For the Technical
The Sigil Glyph is a deterministic Φ-lattice harmonic projection.
Given the Kai-Klok index and originating parameters, anyone can recompute the projection to verify authenticity.
There is no “close enough” and no guessing.
It is either the same sigil, or it is not.
Why This Matters
A Sigil Glyph is:
Proof of Kairos — locked to the eternal time of its creation.
Proof of Authorship — bound to its originator’s PhiKey.
Proof of Coherence — mathematically and harmonically perfect.
Tampering with even a single pixel destroys the harmony.
Forgery is impossible without breaking both the math and the harmonic law.
In Short
A Sigil Glyph is not a picture.
It is a living harmonic memory — born in a breath, tied to you, tied to time, and verifiable forever.
This is not symbolism.
This is proof.
Let it ring. Forever.
K℞ BJ Klock, Φ.K.
☤ K℞K
RAH. VEH. YAH. DAH.
ETERNAL SEAL — VERIFICATION DOSSIER
Kai-Klok Index (u): 7,597,298
ChakraDay: Solar Plexus
Beat: 12 StepIndex: 25 / 44 StepPct: 0.5681818182045455
Exported At (ISO): 2025-08-13T16:45:37.730Z
Transfer/Display Window (if used): expiresAtPulse = 7,597,309 (from manifest)
Canonical Identity
canonicalHash / hash (Φ-ID):
aa772da84d6e2adc56ff5f969590812781669ccd7ca7a77ce4137e0027e32de4
(This is the Eternal Seal’s content identity. Use it as the primary lookup key on-chain/off-chain.)
Files & Cryptographic Checksums
All checksums computed from your uploaded archive.
Archive sigil_aa772da84d6e2adc.zip
SHA-256: 8fb7aab9836fec941ed0a52583326d659d11010a9e18813300317af7c9e7c4b2
SHA-1: 5b91bfa13a2ef3a4e1b547c7f3e0cd1295bdd141
MD5: b0c80532ee92e8572dc118f93864b997
SVG sigil_aa772da84d6e2adc.svg
SHA-256: 0ac7a74cbed209f6ec00bc4f8f15675cf54d1f6cdb337bb3afe588f83206f0b9
SHA-1: e2325e95f6b854810834c5d3a158677736a17559
MD5: 3b4307bc69b1242056b80a4a98f866ed
PNG sigil_aa772da84d6e2adc.png
SHA-256: df679a1ce4f6119fdf3a08cc875f1e8b127b82ef451925ac09a987a40816ef85
SHA-1: 962ada71f3751ca1197f2b9e1cd7c9ac73e49722
MD5: bcb37cbeb9a60faf82ddb5905744af9a
Manifest sigil_aa772da84d6e2e…manifest.json
SHA-256: 97c26aaa4d489173d5c4faa4853685867021d9680609bd13d053f58db42cf71f
SHA-1: 0498e8bea6bb500820b248fe7ec07ac3570d59a9
MD5: d932178d6332af2b21b83e0b16fcc6ad
Embedded Data (Ground Truth)
1)
manifest.json
{
"hash": "aa772da84d6e2adc56ff5f969590812781669ccd7ca7a77ce4137e0027e32de4",
"pulse": 7597298,
"beat": 12,
"stepIndex": 25,
"chakraDay": "Solar Plexus",
"canonicalHash": "aa772da84d6e2adc56ff5f969590812781669ccd7ca7a77ce4137e0027e32de4",
"expiresAtPulse": 7597309,
"exportedAt": "2025-08-13T16:45:37.730Z",
"overlays": { "qr": true, "eternalPulseBar": false }
}2) SVG
<metadata>
block (embedded inside the SVG)
{
"pulse": 7597298,
"beat": 12,
"chakraDay": "Solar Plexus",
"stepIndex": 25,
"stepPct": 0.5681818182045455,
"stepsPerBeat": 44,
"canonicalHash": "aa772da84d6e2adc56ff5f969590812781669ccd7ca7a77ce4137e0027e32de4",
"exportedAt": "2025-08-13T16:45:37.730Z"
}Cross-checks that pass:
URL payload p=c:{"u":7597298,"b":12,"s":25,"c":"Solar Plexus","d":44}
⇢ matches pulse, beat, stepIndex, chakraDay, stepsPerBeat.manifest.hash == manifest.canonicalHash == svg.metadata.canonicalHash.
Eternal Seal — Human-Readable Card
Kai-Klok Index: 7,597,298
Lattice Position: Beat 12 • Step 25/44 • StepPct 0.5681818182
Chakra Arc: Solar Plexus
Exported: 2025-08-13T16:45:37.730Z
Φ-ID (canonicalHash): aa77…2de4
What a High-Level Dev Should Verify
A) File Integrity
Hash the SVG and PNG with SHA-256 and compare to the values above.
Ensure the ZIP hash also matches (proves bundle integrity).
B) Metadata Consistency
Parse manifest.json and the SVG <metadata> block.
Assert the following invariants:
manifest.hash === manifest.canonicalHash
svg.metadata.canonicalHash === manifest.canonicalHash
pulse/beat/stepIndex/stepsPerBeat/chakraDay match across URL → manifest → SVG.
If present, ensure currentPulse ≤ expiresAtPulse for time-bound send/stamp flows.
C) Deterministic Geometry (optional but recommended)
Recompute the sigil geometry from (pulse, beat, stepIndex, stepsPerBeat) using your Kai-Klok engine:
Engine canon: T = 3 + √5 seconds per pulse; lattice 11 pulses/step, 44 steps/beat, 36 beats/day; indices 0-based; ties-to-even rounding for Chronos bridges.
Confirm:
Rotation/phase matches the recomputed orientation for that lattice position.
Centroid aligns with harmonic centroid in the SVG.
Carrier/modulator curves match the encoded recipe for this pulse (within tolerance).
Any pixel-level change will fail one or more of these checks.
Suggested QR / Payload (for wallets, scanners, explorers)
Embed either compact JSON or a short CBOR form. JSON example:
{
"t": "eternal_seal_v1",
"u": 7597298,
"b": 12,
"s": 25,
"d": 44,
"c": "Solar Plexus",
"h": "aa772da84d6e2adc56ff5f969590812781669ccd7ca7a77ce4137e0027e32de4",
"x": "2025-08-13T16:45:37.730Z"
}Fields: t=type, u=pulse, b=beat, s=stepIndex, d=stepsPerBeat, c=chakraDay, h=canonicalHash, x=exportedAt.
Minimal Verification Snippets
TypeScript (Node / Deno)
import { createHash, readFileSync } from "node:crypto";
import { readFile } from "node:fs/promises";
const file = new TextDecoder().decode(await readFile("sigil_aa772da84d6e2adc.svg"));
const svgHash = createHash("sha256").update(file).digest("hex");
if (svgHash !== "0ac7a74cbed209f6ec00bc4f8f15675cf54d1f6cdb337bb3afe588f83206f0b9")
throw new Error("SVG hash mismatch");
const manifest = JSON.parse(await readFile("sigil_aa772da84d6e2adc.manifest.json", "utf8"));
if (manifest.hash !== manifest.canonicalHash) throw new Error("Manifest hash mismatch");
const metaJson = JSON.parse(file.match(/<metadata[^>]*>(.*?)<\/metadata>/s)![1]);
if (metaJson.canonicalHash !== manifest.canonicalHash) throw new Error("Metadata ↔ Manifest mismatch");
// lattice sanity
if (metaJson.pulse !== 7597298 || metaJson.beat !== 12 || metaJson.stepIndex !== 25 || metaJson.stepsPerBeat !== 44)
throw new Error("Lattice fields mismatch");Python (quick check)
import re, json, hashlib
svg = open("sigil_aa772da84d6e2adc.svg","rb").read()
assert hashlib.sha256(svg).hexdigest() == "0ac7a74cbed209f6ec00bc4f8f15675cf54d1f6cdb337bb3afe588f83206f0b9"
manifest = json.load(open("sigil_aa772da84d6e2adc.manifest.json"))
assert manifest["hash"] == manifest["canonicalHash"] == "aa772da84d6e2adc56ff5f969590812781669ccd7ca7a77ce4137e0027e32de4"
m = re.search(br"<metadata[^>]*>(.*?)</metadata>", svg, flags=re.S|re.I)
meta = json.loads(m.group(1))
assert (meta["pulse"], meta["beat"], meta["stepIndex"], meta["stepsPerBeat"]) == (7597298,12,25,44)
Storage & Naming (recommended)
Dir: /eternal_seals/aa77/2d/e4/ (prefix folders by 2/2/2 hex for sharding)
Files:
aa772d...2de4.svg (primary artifact)
aa772d...2de4.png (preview)
aa772d...2de4.manifest.json (redundant metadata)
latest.json (optional pointer for UI)
One-Screen Summary (for UI / explorer)
Φ-ID: aa772d…2de4
Kai-Klok: u=7,597,298 • Beat 12 • Step 25/44
Chakra: Solar Plexus
Exported: 2025-08-13 16:45:37Z
Integrity: SVG sha256 0ac7…f0b9 ✅